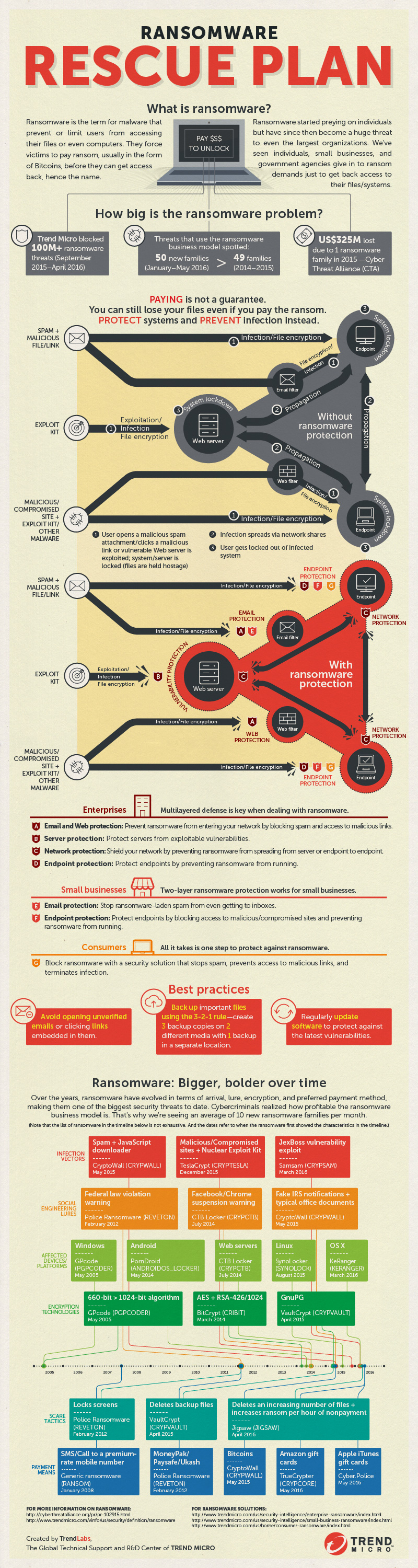
Digital Signage System
Using the
power of the internet, turn any HDMI-compatible TV or device into a dynamic
information and advertising platform.
Simply plug in the small ScreenScape Connect
device, attach to your local WiFi network and the TV will immediately
begin to display the content that you create and maintain online. Manage one screen or an entire network of
devices from your PC, Mac, laptop or tablet.
Plug & Play Digital Signage
If you’ve tried digital signage
before, you know it can be difficult and expensive. But it doesn’t have to be. ScreenScape offers a smarter way to turn any
TV into a dynamic digital sign.
It starts with the ScreenScape
Connect device. This tiny
media player is backed by Dell and features a true plug and play design – no
brackets to mount, no screws to turn. It
draws power from most TVs and connects wirelessly to your network.
There is no operating system to
configure and no software to download. Plug
it in, get it online and control it remotely from your ScreenScape internet account.
Influence Buying Decisions
Digital signage is a proven,
effective way to engage customers and boost sales. Savvy marketers use it to influence buying
behavior where it matters most – in the storefront.
Local digital signage informs
your customer’s buying decisions allowing you to serve them better with a wider
range of options.
Manage Content, Deploy Anywhere
All of your content is stored on
secure, cloud-based servers. This allows
you to manage one or even hundreds of screens from a single ScreenScape internet
account.
Corporate managers can create and
deploy consistent content to all screens while still allowing for local content
that is managed at the local level.
Simple Content Creation
We’ve taken the difficulty out of
digital signage so you can spend your time managing your business. You get access to industry leading content
management software and graphic design services from Cox Printers that makes
publishing easy.
Boost Advertising Revenue
In addition, to your own in-house
content and promotions, ScreenScape allows you to create a
revenue-generating advertising stream. Get paid by your vendors, distributors
or other local businesses to run their promotions on your screens. With a free content-provider account, other
business can create the content and you can manage the times and locations that the content is displayed.
Great Product, Free Perks
Not only is ScreenScape the quickest and
easiest digital signage system to install, but all of these services are
included:
·
Free Device (with a 3-year contract)
·
Free Content Management
·
Unlimited Ads/Content
·
Free Training
·
Free Support
Find out if ScreenScape is right for
you. Call us today for a no obligation
demo at: 844-726-6243